Assalamualaikum and hai bloggers. My name is Effah Mustafa and i'm currently studying in Cosmopolitan College of Commerce and Technology under BTEC Diploma In Business. This will be my first blog and the content will be 100% about my TICT (The Impact of Communication Technology) module. Creating a blog is part of my assignment task and the content will be about internet.
Saturday, 11 August 2018
Thursday, 9 August 2018
Content of P1
INTERNET
As we all know, people and internet can't be separated because this is the only way for them to communicate with other people from outside or inside the country. Based from my opinion, internet is a system that have been created or designed for people to communicate among themselves. Apart from communication, people that used to have a business such as an online seller use internet as their way to communicate with their customer and also the supplier. By using internet, they also can do a business research, promoting their products, advertise their business and many more.How does the internet works?
In order to connect to internet, every computers must have a unique IP address. An IP address is known as Internet Protocol addresses which can be defined in the form nnn.nnn.nnn.nnn where n must be a number from 0-255. The diagram shows how internet connected to 2 different computers. Based from the diagram, in order to connect to different computer, they need a router as an intermediary between internet and the computer itself.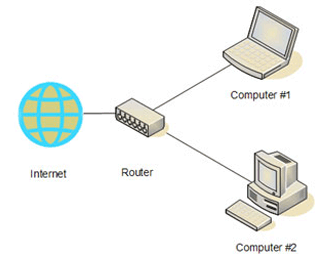 |
| Diagram 1: hows internet connected to different computers |
What is a server?
Based from the research, a server refer to a computer program which provides a service to another computer program and its user. There are few types of server, such as:- An Application Server
- A Proxy Server
- A Mail Server
- A Virtual Server
- A Blade Server and also known as server blades
- A File Server
- A Policy Server
What are the types of tconnection o the internet?
Obviously, there are many ways for an electric device such as mobile phone, laptop and personal computer can connect to the internet. Computer networks come in may forms and there are 3 basic types of network connection, they are:
- Point-to-point: the connections that only allow one device to communicate with one other device.
- Broadcast / multicast: the connections that allow a device to send message and have the copied of that message.
- Multipoint: the connection that allow one device to connect and send messages to any devices in parrallel.
- Fixed Broadband Internet
- Mobile Internet
- Virtual Private Network (VPN)
- Dial-Up Networks
- Local Area Network (LAN)
- Direct Networks
Equipment to set-up internet
 |
| Diagram 2: A Modem |
Modem is a network hardware device that allows a computer to send and receive data over a telephone line or a cable or satellite connection. Internet is usually comes from the telephone line, so in order to connect internet to computer, we need a modem and from modem we can connect internet to computers. Apart from that, there are other equipment that also helps to connect internet from the modem and it known as router.
 |
| Diagram 3: A Router |
 |
| Diagram 4: Networking Cable |
Router is a small, single-purpose computer that receives information from a modem. Using a networking cable, a modem can connect to router and from there can provide a wireless. Diagram 5 shows the stage of the connection from the internet itself until all of the devices using a modem and router.
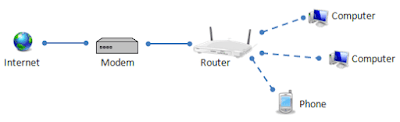 |
| Diagram 5: Modem and router connected |
Internet Service Provider (ISP)
An Internet Service Provider (ISP) is a company which provides an access to the internet and other related services to the individuals and other companies.Protocols
Protocols means the rules and conventions for communication between network services.Domain Names
It is an identification string that are used to identify one or more IP addresses.World Wide Web Consortium (W3C)
W3C which stands for World Wide Web Consortium defines as an international community where member organization work together to develop web standards.Internet Society (ISOC)
Internet Society is a non-profit organization that involved with the internet engineering task force. It was formed in 1992 by Vint Cerf and Bob Khan which also can be knows as "Father of the Internet".World Wide Web (WWW)
World Wide Web is a way to access information through the Internet media. It is an information sharing model built on the Internet. Web uses HTTP protocol, only one of the languages used on the Internet, to transmit data. Web services, which use HTTP to allow applications to communicate to exchange business logic, use the Web to share information. The Web also uses browsers, such as Internet Explorer or Firefox, to access Web documents called web pages that are linked to one another via hyperlinks. Web documents also contain graphics, sound, text and video.World Wide Web and internet in not synonym because WWW is a web where people always use it for researching and many more. So in order to use the World Wide Web, they need an internet to access to their personal device.
Wednesday, 8 August 2018
Content of P2
Using internet for advertising a business is a most common thing that every companies in this world do because by using internet they can do anything for their business such as advertising the business, promoting their business products, communicate with their supplier and customer and many more. In this post, I'm going to include 2 companies which are TelBru that comes from Brunei Darussalam and Pizza Hut that comes from America.
Communication is one of the way that most of business do in order to communicate with their supplier and also to attract customer to buy their company products. TelBru is one example of a Brunei company that use communication to communicate with their customer. One of the example of communication in TelBru is telephone. Since TelBru is a service company that provide a WiFi for people, so possibly people will contact them if they have any problems regarding their WiFi. Another example of communication that they use is social media. One of the social media that they use is Instagram. By using Instagram, they can keep updating any latest quota WiFi and also updating if there is some promotion for that month. Apart from that, they also use email to send their customer's bill payment, notification if there is any problem on their WiFi and also every month they will remind their customer about their bill payment or an outstanding payment through email.
Procurement
Procurement is a way of people buying and selling through online. For TelBru, if their customer's WiFi quota is already finished, they still can buy an additional quota. TelBru also provide an apps for their customer's convenience. By using the TelBru apps their customer can pay their bill payment through online.
Business Research
Business Research is the process of collecting data and information for the purpose of making business decisions. TelBru have provide a questionnaire for their customer. Since TelBru have a customer service department. Using the questionnaire, they will know if there is any customer that not satisfied with their services or they will know if there is any lackness in their company.
Promotions
Every business need to make a promotion every month or every week in order to make their customer being loyal to their company. TelBru also provide a promotion every month to their customer. One of the latest promotion that they provide is the 2 days unlimited which is launched last month on May.
TelBru
As a major telecommunications
company in Brunei Darussalam and a leading service provider for fixed line,
broadband services, line and data services for rent, TelBru has set a strategic
direction and developed a comprehensive plan to achieve its objective of
building a telecom business successful, sustainable and profitable.
Telekom Brunei Berhad(TelBru) was
established on the 30th May 2002 under the Company Act Chapter 39 as
a Public Limited Company and has been fully operational since April 2006 when
Department of Telekom Brunei(JTB) was corporatized on 1st April
2006. TelBru advertised the job hiring on their Facebook page, their company
website, and newspaper and also by joining any expo where many people can find
a variety of company and send their application form to that company
 |
| Diagram 6: logo of TelBru |
How TelBru use internet for their business?
Basically, there are 4 ways of using internet for every business, they are:
- Communication
- Procurement
- Business Research
- Promotion
Communication is one of the way that most of business do in order to communicate with their supplier and also to attract customer to buy their company products. TelBru is one example of a Brunei company that use communication to communicate with their customer. One of the example of communication in TelBru is telephone. Since TelBru is a service company that provide a WiFi for people, so possibly people will contact them if they have any problems regarding their WiFi. Another example of communication that they use is social media. One of the social media that they use is Instagram. By using Instagram, they can keep updating any latest quota WiFi and also updating if there is some promotion for that month. Apart from that, they also use email to send their customer's bill payment, notification if there is any problem on their WiFi and also every month they will remind their customer about their bill payment or an outstanding payment through email.
 |
| Diagram 7: TelBru's Instagram |
Procurement is a way of people buying and selling through online. For TelBru, if their customer's WiFi quota is already finished, they still can buy an additional quota. TelBru also provide an apps for their customer's convenience. By using the TelBru apps their customer can pay their bill payment through online.
Business Research
Business Research is the process of collecting data and information for the purpose of making business decisions. TelBru have provide a questionnaire for their customer. Since TelBru have a customer service department. Using the questionnaire, they will know if there is any customer that not satisfied with their services or they will know if there is any lackness in their company.
Promotions
Every business need to make a promotion every month or every week in order to make their customer being loyal to their company. TelBru also provide a promotion every month to their customer. One of the latest promotion that they provide is the 2 days unlimited which is launched last month on May.
 |
| Diagram 8: TelBru's Promotion on May |
Pizza Hut Inc
Pizza Hut is a fast food company which serve a variety of pizza. It was founded in 1958 in America by brother Dan and Frank Carney. Overall pizza hut have 13,728 branches worldwide. In Brunei Darussalam, there are more 20 branches of pizza hut. |
| Diagram 9: logo of Pizza Hut |
How Pizza Hut use internet for their business?
Pizza Hut use the same ways of using internet like TelBru, which are:- Communication
- Procurement
- Business Research
- Promotion
Communication
Pizza Hut also another company that use communications in order to communicate with their customers. They also use a social media to advertise their company and promote their products. Apart from that, they also advertise their company through the cinema screen. The advertising will appear before the movie start. By doing this kind of advertising, people in cinema will get attracted and from there the people will automatically plan to eat their lunch or dinner there. Pizza Hut also have their company telephone so that their customer can directly call them if they wish to buy any pizza and want it to be delivered to their home. |
| Diagram 10: Pizza Hut logo |
Procurement
Pizza Hut also have their own website for their customer to buy the pizza through online. In their website, they already provide group of food so that the customer can easily choose the menu. Apart from that, they also have their company email. This email is for updating their customer's order and also they will send the receipt of the bill payment.
Pizza Hut also have their own website for their customer to buy the pizza through online. In their website, they already provide group of food so that the customer can easily choose the menu. Apart from that, they also have their company email. This email is for updating their customer's order and also they will send the receipt of the bill payment.
 |
| Diagram 10: Pizza Hut Website |
Promotions
Pizza hut also make a promotion every month for their customers. This an make people get more attracted to buy their pizza. One of the promotion that available 2 months ago is buy one regular pizza and one hershey chocolate chip with the price of $24.90.
 |
| Diagram 11: Pizza Hut Promotions |
Tuesday, 7 August 2018
Content of P4
For the next pass criteria, the learners need to describe
how they took precautions to reduce the risk to security inherit in working
on-line, for each process. This should include:
- Setting Up Passwords
- Checking Before Downloading Emails
- Backing Up Data
- Taking Precautions Over Security of Data
For this question, I’m going to describe 2 process which are
setting up passwords and checking before downloading emails.
- Setting Up Passwords
Passwords is the important thing that should have in our
devices such as mobile phone, laptop and personal computer. Other than that,
our account either it is a bank account or email account also need a password.
For bank account, the passwords are in terms of number pin. While, for the
devices can be in terms of pin, pattern or passwords. It is important to have a
password because it can avoid any hackers to hack our devices and also to avoid
them to stole our personal data and all the important documents. You need to be
more creative to set your password because an easy password can be access by
any hackers. So, you need create a strong password especially for your bank and
email account. It is important to create a strong number pin for your bank
account because in there you’re putting your money inside it. While, for the
email account it is also important because in there will have your important
documents that either you received it from people or you send it to people.
Below, I will show how to make a password in laptop.
Step 1:
 |
| Figure 1: Windows |
As shown, you need to open your windows and find the setting
apps. From the picture, the one that I circle is my setting apps and then click
it.
Step 2:
 |
| Figure 2: Windows Setting |
After you open your windows setting, you need to find
“account” program and open it.
Step 3:
 |
Figure 3: Accounts Setting |
Based from the picture, you can see in the “accounts”
program have your info, email & app accounts, sign-in options, access work
or school, family & other people and sync your settings. Among all of that,
you need to click the “sign-in options”.
Step 4:
 |
| Figure 4: Sign-In Options |
In the “sign-in options”, you can see password and pin. So,
for your laptop password you can choose either you want to use password or pin.
- Checking Before Downloading Emails
Downloading documents is a common thing that most people do
nowadays. Most people especially employees download documents through email
because they use email to send an urgent and important document to other
company or to their manager. Apart from business, college also use email to
send assignment to students. Before we download email, we need to check it
first so that we are not wasting our time to download a wrong document. Those
pictures here are the example of checking before downloading emails using my class
Gmail account.
 |
| Figure 5: The Gmail Inbox |
 |
 |
| Figure 6: Gmail Message |
So, as you can see this is the contain of the message. She
sends a message to inform us that she is sending the slide and also, she sends
the attachment of the slide. In order to check it before download, I need to
open it online to make sure that it is the correct slide.
 |
| Figure 7: Content of the Message |
This picture shows the slide that she sends to us. So, since
I’m already sure that she sends a right slide, I can straight away download it
and save it to my assignment folder.
Monday, 6 August 2018
Content of P3
For the pass criteria, the learners should carry at least 2 process from each section of the unit content:
Above is also the picture where I send a letter to SDY
Company to publish a novel. SDY Company is a company that specialized for
people to publish their books and novels. In that picture is the conversation
between me and one of the employees in SDY Company. We are talking about the
price and the package that they prepare. In the end, we made a meeting where we
can discuss more about the novel synopsis, price and also the package included.
- Methods of backing up data
- Send emails using business language and protocols
- provide evidence of shopping transactions
For this question, I’m going to choose methods of backing up
data and send emails using business language and protocols
1. Methods of backing up data
1. Methods of backing up data
Backing up data is a method of avoiding you from losing all
of your documents either in your mobile phone, laptop and your personal
computer. There are many ways of backing up data, they are:
- USB Stick
- External Hard Ware
- Time Machine
- Network Attached Storage
- Cloud Storage
- Printing
 |
| Figure 1: USB Stick |
Most people called USB stick as a pendrive. It is a cheap
and convenient sticks where people can bring it along with them because the
size is small. It is easy to put our files and documents in there but then it
also easy to lose it. The advantage of the USB Stick is can easily transfer
data to other sources and also it is extremely portable. while the disadvantage
is it can easily lose since the size is small.
External Hard Ware
 |
| Figure 2: Hard Ware |
External hard drives are what they sound like hard drives
left outside your computer, meaning they can be installed to other sources. If
using it for backup, it is best not to use it as an “extra per day hard drive”.
Using the external hard ware can give many advantages to people because it is
also cheap like USB stick and also, we can put so many documents in there since
they have provided a plenty of storage space for larger files. Meanwhile, it
also can give a disadvantage because it can open problems which lost files in
the first place by a power surge or malware.
Time Machine
 |
| Figure 3: Time Machine |
Time machine is specialized for the Mac users only. It is an
option where it can backup files automatically to the external hard drives.
Apple company sells their brand of dedicated Time Capsules but still can use
any hard disk for it. By using this method, it will automatically keep backups
for the last 24 hours, daily for the last month and then weekly backups until
the machine is full. The advantage using time machine is it frequency of
backups means you should never be too out of date. Also, it can back up the
whole drive and not just the key files. While, the disadvantage is only the Mac
user can use the time machine and also it is quite expensive.
Network Attached Storage
 |
| Figure 4: Network Attached Storage |
This method usually most of businesses use it because they
tend to use this method to backup their files but then when there are so many
homes have multiple computers, the idea has a certain appeal, especially for
those looking to save files from more than one source. The advantage for this
is it can work with phones and tablets but then the price is quite expensive.
Also, it can be awkward to set it up and maintain.
Cloud Storage
 |
| Figure 5: Cloud Storage |
There are many types of cloud storage that people can use
such as iCloud, Dropbox, Google Drive and OneDrive. These cloud storages can be
done automatically and also certain amount of space is usually free. Meanwhile,
it can be disadvantages to people because it requires an internet connection to
work and also, companies aren’t obliged to keep these services around forever.
Printing
 |
| Figure 6: Printer |
Printing offers you a hard copy of your most important
documents which can survive power outages. Apart from that, they are easy to
store and access even if your computer is out of action for a few days. It can
give advantage using printing because a backup that won’t affected by hardware
outages or tech headaches and also it is so impossible for hackers to access
our files and documents. However, there also have a disadvantage of using
printing. One of them is sometimes it can be awkward to manage for people that
don’t have any experience of using printer. Other than that, it can be
impossible to print for certain file types.
2. Sending emails using business language and protocols
I’m going to describe the second process which is about send
emails using business language and protocols. Below, I’m going to insert two
screenshot pictures about my conversation with one of the companies in Brunei
Darussalam and also with the SDY Company.
 |
| Figure 7: Sponsorship Proposal |
Above is the picture where I send a letter to one of the
companies in Brunei Darussalam. The letter regarding about looking for a
sponsorship. MIM Company wish to do a charity event which they name it as
cancer run event. In order to run the event smoothly, they need a sponsorship
from other companies. On the pictures, it shows that the company willing to
give $3,500 and also, they offering of sharing profits of 50% from the products
that they sell on the actual day.
 |
| Figure 8: Publish Book Letter |
Sunday, 5 August 2018
Content of M1
Here I’m going to post 4 videos that carried different
problems and solution.
1. Spam Message.
This video shows about a problem that nowadays most of people faced it. We called it as spam message. Spam message can be defined as a commercial advertising in terms of economical. Usually, they send the spam message through email especially Gmail because email is a highly effective medium for senders. The effects of getting a spam message is it can give more indirect and serious effect on email services and their users. So, the solution for this problem is already state in the video itself. First step, you need to open your google account. After that, you need to find the spam folder and then click it. So, from there you can see all of your spam message that you received. In order to avoid something bad happen in the future, you need to at least blocked the user Gmail. Based from the video, the user name that send the spam message to my google account is promotion GG. The first thing you need to do if you want to block it, you need to find the small arrow at the left side and then click it. After that, find block button and click it. And, finally you're successful block it.
2. Error Message
Here I’m going to post 4 videos that carried different
problems and solution.
2. Error Message
The second video shows the second problem which is error
message. Error message is usually happened when someone try to type a wrong
word in the search box. In a business, we need to avoid error message because
when you’re trying to make a brochure or leaflet about your product price then
you accidentally wrote a wrong price. This can lead to dissatisfaction among
their customers. The example that I use in the video is search about
amazon.com. You will receive an error message if you accidentally type the
wrong for example instead of type “amazon.com”, I wrote it as “amaypn.com. So,
from there you can see the error message appear. In this case, the error
message is stating “this site can’t be reach”. So, in order to solve this, you
need to recheck your spelling. When you already sure that your spelling is
correct, you can click the enter button and then they will give you the right
website page.
The third video shows another problem which we called it as
non-delivery email. Non-delivery email usually happens when you’re trying to
send a document to your partner account but then you misspell it without your
knowledge. It is important to avoid this problem because if the documents that
you’re trying to send to another company is an important document but then you
send it into a wrong and misspell email, the person in that company will not
receive it and this can create miscommunication among two companies. For
instance, I’m trying to send a query letter to publish a novel to one of the employees
in SDY Company which his email account is “syahwandani.sd@gmail.com”.
But then, suddenly a message appears which state “address not found”. When I
received the message, I realized that I misspell the email. I wrote it as “syah3wandani.sd@gmail.com”.
So, the solution for this problem is you need to check your spelling and if you
already sure that you’re correct then you can click the send button.
4. Too
many hits on search engine
Too many hits on search engine can waste your time because
if you want to search something you need to be more specific and straight
forward. It is important for a company to avoid this because for instance they
want to search about the location of their partner company. So, if they just
type “location” they will get a lot of result about location. So, they will
waste their working time on scrolling the web page in order to find the correct
page. So, in order to avoid and not waste their time, they need to type the
keywords which is “location of SDY Company”. From the video I’m trying to
search about buttermilk chicken recipe but then I just search chicken recipe.
So, from there I will receive so many results about chicken recipe. This can
waste your time scrolling to find a right web page. In order to n avoid wasting
time, I need to type the keywords which is buttermilk. So, they will give me
the right website page.
Subscribe to:
Comments (Atom)
